Cyberproofing rail: Are your rail systems ready for Australia’s cyber regulations?
By Jorge Aldegunde, Global Railway Technical Manager, DNV & Darragh Downey, Founder, O/IT Cyber
To help rail operators, suppliers, and integrators navigate this increasingly complex landscape, DNV launched the Cyberproofing Rail webinar series. Across three episodes, we explore how rail organizations can turn policy into practice, covering global frameworks, technical controls, and the collaboration needed between safety and IT/OT teams.
If a cyberattack shut down signalling across Sydney’s busiest rail corridor tomorrow, how quickly could operators detect, respond, and recover?
With cyber threats against critical infrastructure escalating globally, this is no longer a hypothetical scenario. Digitalization has transformed everything from signalling to passenger information systems, making cybersecurity not just a technical issue but a core safety and operational concern.
Across the globe, regulators are raising the bar. Europe’s NIS2 Directive, the Cyber Resilience Act (CRA), and sector-specific frameworks such as TS 50701 show a clear trend: securing operational technology (OT) in rail is moving from optional to mandatory.
Why we launched the Cyberproofing Rail webinar series
To help rail operators, suppliers, and integrators navigate this increasingly complex landscape, DNV launched the Cyberproofing Rail webinar series. Across three episodes, we explore how rail organizations can turn policy into practice, covering global frameworks, technical controls, and the collaboration needed between safety and IT/OT teams.
Australia: Navigating dual compliance challenges
Episode 1, “Are your rail systems ready for Australia’s cyber regulations?”, aired on 30 July 2025 and spotlighted the unique Australian context.
Operators here face the dual challenge:
- Complying with domestic obligations such as the SOCI Act and AS7770.
- Managing influences from European frameworks like IEC 62443, CRA, and TS 50701, especially given the reliance on European suppliers and integrators.
Australia’s regulatory response is anchored in AS7770 and the SOCI Act, which together form the foundation of cybersecurity governance for the nation’s critical rail infrastructure.
- AS7770 sets out architectural principles such as “defence-in-depth” and requires board-level accountability.
- SOCI Act introduces strict obligations, including a 12-hour reporting window for critical cyber incidents – one of the shortest globally.
As Darragh Downey noted: “Insider threats, cloud system vulnerabilities, and recovery planning aren’t fully addressed in AS7770. Rail operators must go beyond baseline requirements to achieve true resilience.”
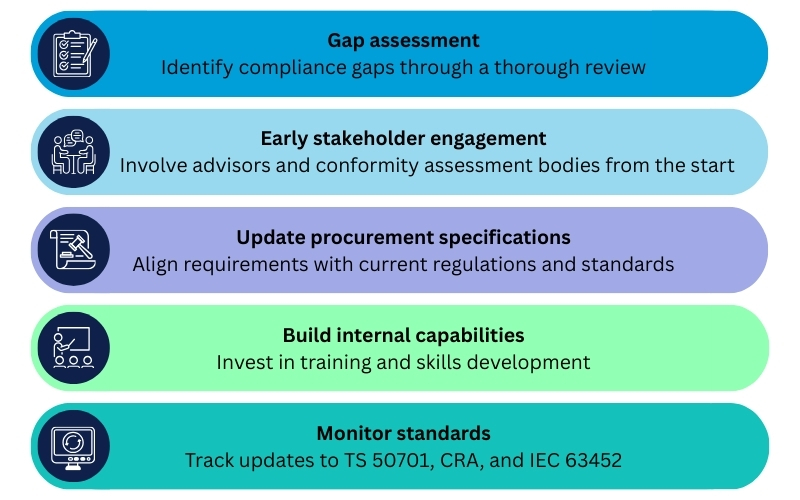
From compliance to resilience: Closing the gaps
Bridging the gap between compliance with real-world implementation is where many organizations struggle. In this episode, we discussed key frameworks:
- IEC 62443: A lifecycle-wide approach that supports SOCI compliance and aligns with international OT cybersecurity best practices.
- IEC 63452 (emerging): A new standard under development to address lifecycle gaps not covered today.
Yet most stakeholders are still at an early stage, with common gaps in:
- Asset visibility.
- Supplier assurance
- Organizational capability.
As Jorge Aldegunde emphasized: “Cyber resilience in rail demands more than checkbox compliance. It requires strategic foresight, cross-disciplinary coordination, and ongoing investment.”
Building your cyber resilience roadmap
Cyber resilience in rail goes beyond compliance checklists. The roadmap must include:
- Strategic foresight: Anticipating evolving threats and regulatory shifts.
- Cross-disciplinary coordination: Bridging IT, OT, safety, and governance.
- Ongoing investment: in people, processes, and technology.
9/12/2025 11:20:00 AM





