The need for cybersecurity is being driven by megatrends including digitalization of society, geopolitics and multiple simultaneous crises, and a rising tide of cyber-crime, sometimes state-sponsored and with large resources.
As companies’ IT and operational technology (OT) systems increasingly interconnect with each other and externally, they must manage thousands of identities used for authentication and access. The identities include internal users, external partners, contractors, applications, bots, and devices.
On the plus side, digitalization and connectivity can spur efficiency, profitability, and innovation. But they also bring complexity to cybersecurity, with each identity being a potential entry point for cyber attackers. Malicious actors use compromised digital identities to access networks and move around, trying to gain more privileged access to wreak havoc and maybe hold companies to ransom.
Identity and access management is critical for business resilience
Modern Identity and Access Management (IAM) based on robust Identity Governance and Administration (IGA) has therefore become essential to managing digital identities for cyber and hence overall business resilience and regulatory compliance.
‘Unmanaged identities’ was the most cited identity-related blind spot in organizations in a poll of participants at a recent DNV-led webinar on IAM/IGA.
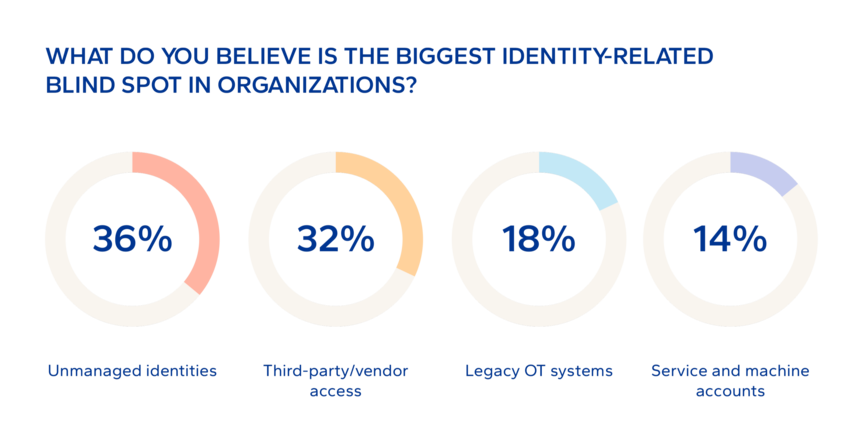 Source: Poll at June 2025 DNV Cyber webinar "who has access to what?"
Source: Poll at June 2025 DNV Cyber webinar "who has access to what?"
The webinar drew on DNV Cyber’s whitepaper Who or what has access to what?, which analyses challenges and IAM/IGA solutions. In another poll of attendees, ‘user experience versus security and privacy’ was the most cited challenge for organizations in managing digital identities.
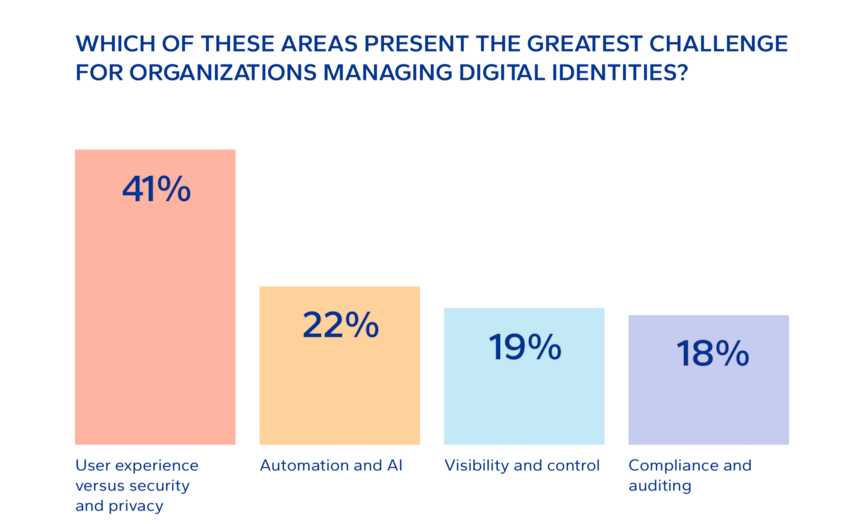
Source: Poll at June 2025 DNV Cyber webinar "who has access to what?"
In discussing how to meet the top challenges identified in the polls, participants heard that a multi-pronged approach is required to balance user experience with security, privacy, and issues in access management. The key message was that robust IAM solutions can streamline access control and enhance visibility without sacrificing user experience.
Panellists were adamant that there should be no compromises on cybersecurity. Speaking in a personal capacity, Stein Ove Røv, Strategic Advisor & Head of Crisis Management, Digitalization and IT at Norway’s Skagerak Energi said: “Security should be number one regardless of user experience and any impact on innovation.”
Driving the need for cyber resilience
Energy companies take cyber threats seriously. In DNV Cyber’s Energy Cyber Priority 2025 research, two-thirds (65%) of sector professionals said their leaders see cybersecurity as the greatest current risk to their businesses. There is mounting concern over multiple threat actors: more than two-thirds of professionals in each case were anxious over organized cyber-criminal gangs, foreign powers and state-sponsored hackers, human error, and hacktivists.
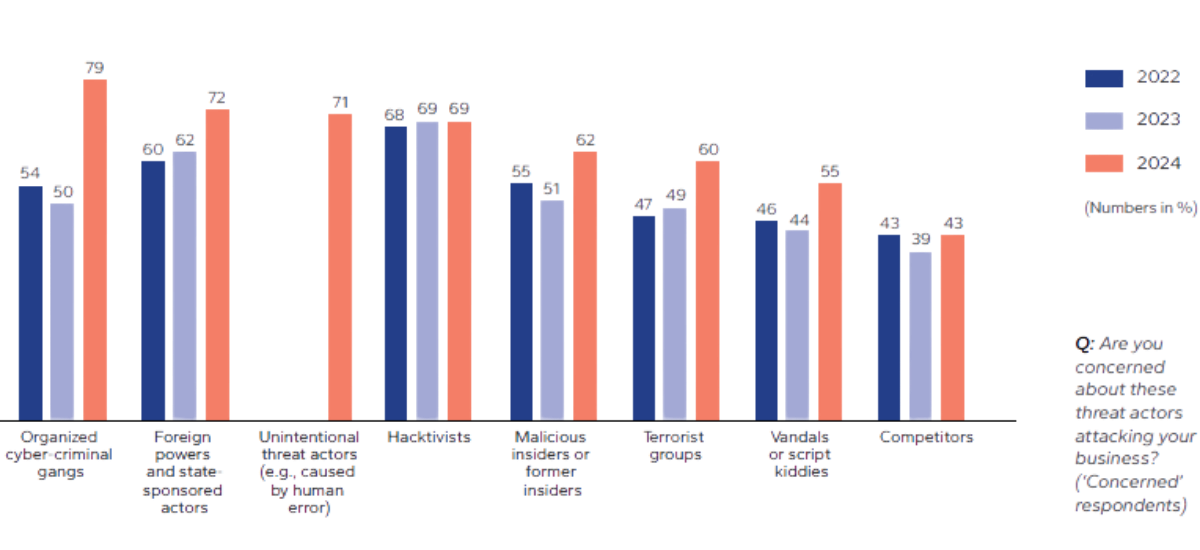
Concern is rising among energy professionals over a range of cyber threat actors
(Source: Energy Cyber Priority 2025, DNV Cyber)
“This supports our view that managing human and non-human digital identities across all environments is one of the greatest business resilience challenges facing energy and other industries,” said Veera Relander, Head of Business & Delivery Management at DNV Cyber.
Identifying challenges in IAM/IGA
Webinar participants heard about key challenges in optimizing IAM, as underlined in the paper Who or what has access to what?
The obstacles include, among others, limited visibility on who has access to what systems and data; inconsistent joiner-mover-leaver processes; relying too much on manual controls and outdated directory services; and weak control of privilege escalation and dormant admin accounts.
Offering solutions in IAM/IGA
Participants also heard how organizations can overcome human, organizational and technological issues to optimize cyber resilience while complying consistently with regulations such as the EU’s NIS2, GDPR, CRA, DORA, and AI Act as applied to various industries.
“While awareness of the challenges is rising up the leadership ladder in organizations, we are still encountering energy clients unaware of regulatory requirements for cybersecurity in their sectors,” noted Carl Christopher Kiønig, Business Community Lead at DNV Cyber.
Who or what has access to what? describes proactive and strategic approaches based on robust IGA programmes as the foundation for modernized, resilient IAM through ensuring that the right individuals or machines have the right access at the right time, and nothing more.
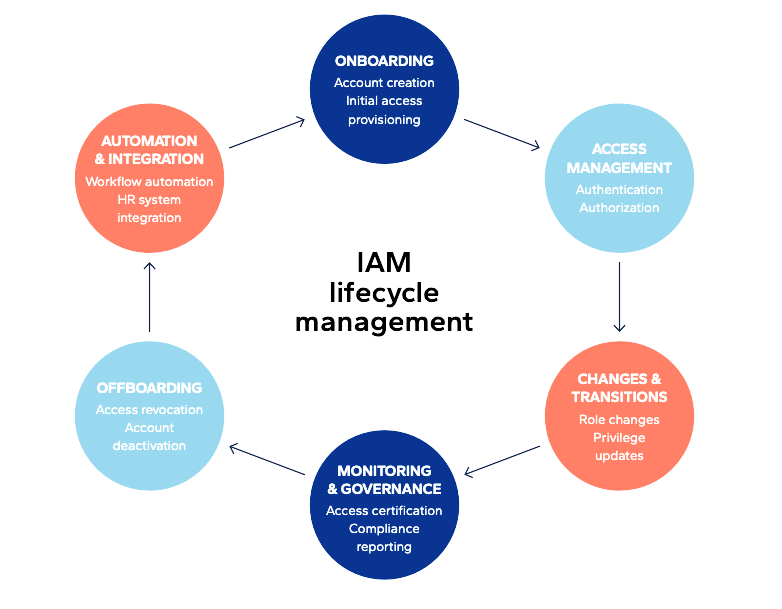
Strategic approaches to IAM and IGA
(Graphic: DNV Cyber from Who or what has access to what?)
At the heart of these approaches are zero trust and least privilege, identity lifecycle management, AI and automation in IAM, and managing third-party and supply-chain risks.
“But when starting out, look at standards and best practice for your sector,” advised DNV Cyber’s Kiønig. “For IT, it’s quite easy: ISO 27001. For OT, there’s material like DNV RP-G108 and IEC 62443. If you’re considering renewing, upgrading or implementing identity controls, do a maturity analysis for which there are lots of tools available online, and some best practices. Then you will at least have a starting point.”
ISO 27001 is for Information Security Management Systems. IEC 62443 standards cover cybersecurity for industrial automation and control systems. DNV Recommended Practice RP-G108 provides guidance on applying IEC 62443 in the oil and gas industry.
Future-proofing IAM
Who or what has access to what? covers next steps including committing to a holistic approach integrating identity governance into all aspects of the organization.
The paper urges investment in ‘scalable, flexible solutions that can evolve with the organization’s needs, offering adaptability and resilience as digital landscapes grow’.
A third pillar of strategy is continuous evaluation and improvement of identity governance practices, ensuring they are dynamic and able to respond to emerging risks and regulatory requirements.
Who should ‘own’ identity governance?
Getting buy-in from C-suites and boards to commit to optimal IAM/IGA is crucial, the webinar heard. One panellist emphasized the difference between understanding the need for action and truly acknowledging it. Many organizations have fairly immature IAM and view it as a technical function within IT rather than a strategic business resilience issue.
Panellists agreed that for optimal IAM, accountability should lie not only with IT but should be shared with cybersecurity, operations, HR, and business leadership while ultimately being the responsibility of human resources. “But if there’s one takeaway message, it’s simply to fix your IAM – it can have a huge impact,” said DNV Cyber’s Veera Relander.








