Frontline Insights: The Norsk Hydro cyberattack – a reflection on the importance of securing digital identities
A reflection on the importance of securing digital identities
A reflection on the importance of securing digital identities
In today's digital age, robust cybersecurity measures are essential. The cyberattack on Norsk Hydro highlights the vulnerabilities in our interconnected world and the need for strong Identity and Access Management (IAM) protocols. This incident, involving the LockerGoga ransomware, serves as a cautionary tale for industries worldwide, emphasizing vigilance and preparedness against sophisticated cyber threats. By examining this attack and its aftermath, we gain valuable insights into strategies to fortify our defenses.
Protecting against cyberattacks accessing IT and operational technology (OT) is a growing priority among energy industry leaders. Over the last three years alone, DNV research has shown rising concern among such professionals about all cyber threat actors. Criminal gangs and state actors are a particular worry but so are current and former insiders who unintentionally or maliciously compromise security – for example, through revealing passwords or responding to phishing emails.1
Concern has increased among energy industry leaders about all cyber threat actors including current or former insiders
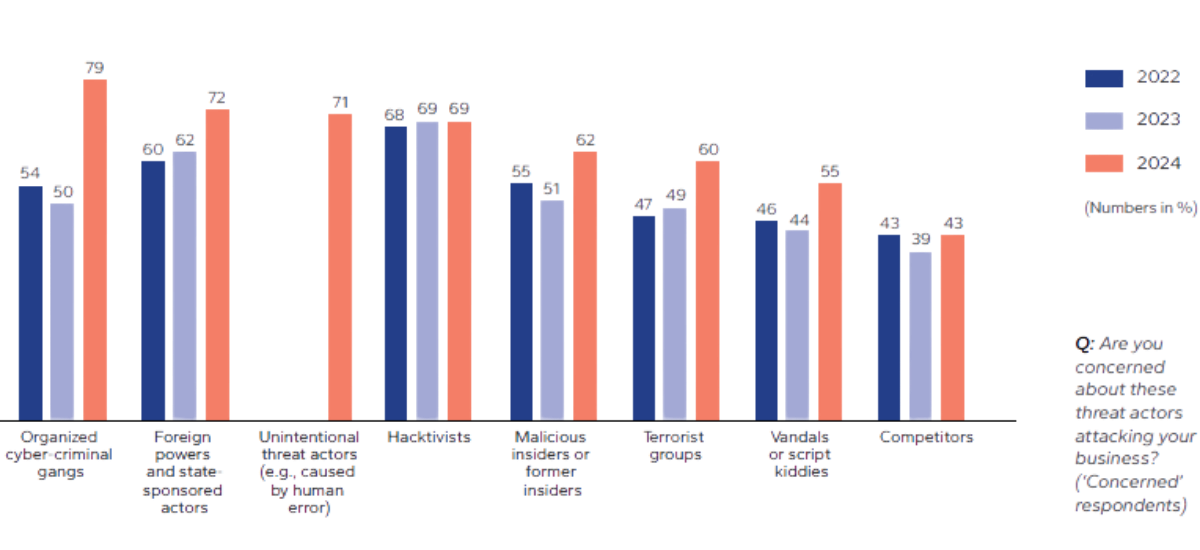
Source: DNV Cyber - Energy Cyber Priority 2025
These justified concerns have coincided with high-profile examples of attackers exploiting weaknesses in Identity and Access Management (IAM) to spread further throughout IT systems to access critical systems once they have penetrated the initial defences.2,3
IAM ensuring that only authorized people can access critical resources is a key pillar of robust cybersecurity strategy that integrates good endpoint security, good network security, proper monitoring, threat detection and response, and security awareness. “That said, many organizations still struggle with even fairly immature IAM and see it simply as a technical function within IT,” says Veera Relander, Head of Delivery & Business Management, DNV Cyber.

Learnings from the frontline
‘War stories’ from the cybersecurity frontline illustrate the risks of failures in IAM for those holding roles such as CIO, CISO, Head of IAM, Director IT and Cybersecurity, and so.
The growing casebook includes the incident in which global aluminium and renewable energy company Norsk Hydro ASA was hit by a LockerGoga ransomware attack in 2019. The malware infected the IT systems and severely disrupted global operations.4
This attack and the solutions remain instructive reading for those planning to govern access and to prepare for and prevent, detect and respond to attacks that exploit systemic or isolated/incidental weaknesses in IAM.
The attack and its impact
On gaining deep access, the attackers deployed the advanced ransomware LockerGoga to encrypt critical files and systems. Unlike other ransomware, LockerGoga also locked out user accounts, preventing IT teams from accessing infected systems, crippling Norsk Hydro’s ability to respond quickly.
LockerGoga’s encryption of critical files and systems made computers and servers unusable. The attack affected 22,000 computers in 170 locations across 40 countries. By preventing Norsk Hydro IT teams from accessing infected systems, the effects were amplified. Automated production lines were shut down, forcing factories to shift to manual operations using pen and paper. The company had to halt key business processes, leading to massive financial losses. The hackers demanded a ransom payment in exchange for decrypting the files.
Responding to the attack
Thanks to its foresight, Norsk Hydro was able to restore its systems from backups. The company collaborated 24/7 internally, and externally with cybersecurity experts, law enforcement, and Microsoft, to investigate and mitigate the attack. Norsk Hydro divulged that all PCs and servers across the company were reviewed, cleaned of any malware and safely restored, according to strict guidelines to ensure security and safety. It added that encrypted PCs and servers were rebuilt based on backups, and the company’s security team was reorganized to better detect and respond to cyber incidents.
It emerged that one Norsk Hydro business area had suffered the most significant operational challenges and financial losses. The company revealed that with the help of work-intensive workarounds and manual procedures, its other business areas maintained almost normal production.
Norsk Hydro openly shared information about the attack, which helped improve cybersecurity awareness across industries. The cost of the incident was USD 70 million, but the company emerged as a model for effective ransomware response, and did not pay the ransom.
Key takeaways from the Norsk Hydro cyberattack

Broader lessons
“This incident highlights how gaps in identity and access management (IAM) — including potential weak authentication, insufficient privilege controls, and limited behavioural monitoring — can enable attackers to escalate privileges and cause widespread damage,” says Pascal van Vugt, Delivery Lead IAM, DNV Cyber. “The attackers exploited stolen credentials, escalated privileges, and used trusted admin tools to move laterally. Weak identity segmentation and over-permissioned accounts amplified the damage. It’s a clear reminder that strong IAM controls are essential for both prevention and response.”
| Challenge | Key questions |
|---|---|
ChallengeVisibility |
Key questions
|
ChallengeCompliance |
Key questions
|
ChallengeEfficiency |
Key questions
|
References
1 DNV Cyber (2025). ENERGY CYBER PRIORITY 2025: Addressing evolving risks, enabling transformation
2 Security update. Uber Technologies, 19 September 2022 [online]. https://www.dnv.com/cyber/insights/articles/frontline-insights-lessons-from-the-uber-2022-data-breach/
3 Updated Okta Statement on LAPSUS$. Okta, 22 March 2022 [online] www.okta.com
4 2019: Cyber-attack on Hydro. Norsk Hydro, 11 June 2021 [online] www.hydro.com

Whitepaper addressing the challenges of securing digital identities – both human and non-human

Free assessment that provides actionable insights and practical recommendations on your IAM posture

Real world examples how DNV Cyber has helped organizations overcome their IAM challenges

Expert reflections and comments on cybersecurity incidents

Who or what has access to what? The importance of securing digital identities