Frontline Insights: Lessons from the Uber 2022 data breach
The 2022 Uber data breach stands as a compelling example of the importance of cybersecurity, revealing the vulnerabilities even major tech companies face.
The 2022 Uber data breach stands as a compelling example of the importance of cybersecurity, revealing the vulnerabilities even major tech companies face.
Few incidents have drawn as much attention as the Uber data breach of 2022. This event not only highlighted significant vulnerabilities within the company's digital identity framework but also underscored vital lessons for the entire industry. As cyber threats evolve at an unprecedented pace, vigilance is more crucial than ever.
The 2022 Uber data breach stands as a compelling example of the importance of cybersecurity, revealing the vulnerabilities even major tech companies face. This sophisticated attack underscores the need for robust security measures and highlights the critical role of employee awareness and training in safeguarding sensitive information. Join us as we delve into the intricacies of this cyber 'war story' and extract valuable lessons to help fortify your organization's defenses against future attacks.

With cyberattacks hitting the headlines more frequently and across multiple industries, companies are paying greater attention and investing more in cybersecurity both for their IT systems and operational technology (OT).
But for all the hardware and software barriers available, one of the cyber weaknesses hardest to control is human error, particularly when people are confronted by increasingly sophisticated and complex cyberattacks that are now being assisted by artificial intelligence.
Lax cyber-hygiene on the part of inadequately trained present or past employees, or outsiders such as suppliers who legitimately have access credentials, can unintentionally give malicious actors what they need to penetrate cyber defences.
Failing to keep passwords secure, or responding to phishing emails and social media messages, are two potential areas of weakness. A recent study found more than a third of cyber breaches at critical infrastructure businesses could be traced back to human error.1
DNV research finds three-quarters (75%) of energy professionals see employees as the weakest link in their organizations’ cybersecurity.2 More than a quarter (27%) of the professionals surveyed indicate that their companies do not run sophisticated phishing tests on employees.
Percentage of energy professional who believe artificial intelligence helps hackers to create more sophisticated phishing attempts

Figure 1, Source: DNV Cyber - Energy Cyber Priority 2025
Such concerns highlight how the best defence strategy is good endpoint security, good network security, proper monitoring, threat detection and response, and security awareness.
Some of the threats are highlighted in the sophisticated 2022 cyberattack in which a social engineering technique unlocked the door for a hacker to penetrate the IT network of Uber Technologies, best known for its ride-hailing services.3 It is one of several cyber ‘war stories’ that illustrate the importance of employee awareness and training in cybersecurity.
In this case, a young hacker possibly associated with cybercriminals purchased access credentials stolen from an Uber employee, but discovered the company’s IT network was protected by multi-factor authentication (MFA).
The attacker repeated MFA push notifications until a targeted employee accepted one out of annoyance or confusion.
In the Uber case, the hacker contacted the employee via an online messaging app, pretending to be from Uber to persuade the worker to comply with a fake authorization request. This social engineering method allowed the hacker to gain access to Uber’s intranet.
The hacker found Microsoft PowerShell scripts on a network share, and the scripts had hardcoded privileged access management (PAM) admin credentials. A schematic representation of the attack is shown in the visual below.
Uber appears to have been fortunate in that the attacker seemed interested only in publicizing that he had been able to hack the system: no ransom is reported to have been demanded.
How the 2022 cyberattack on Uber developed
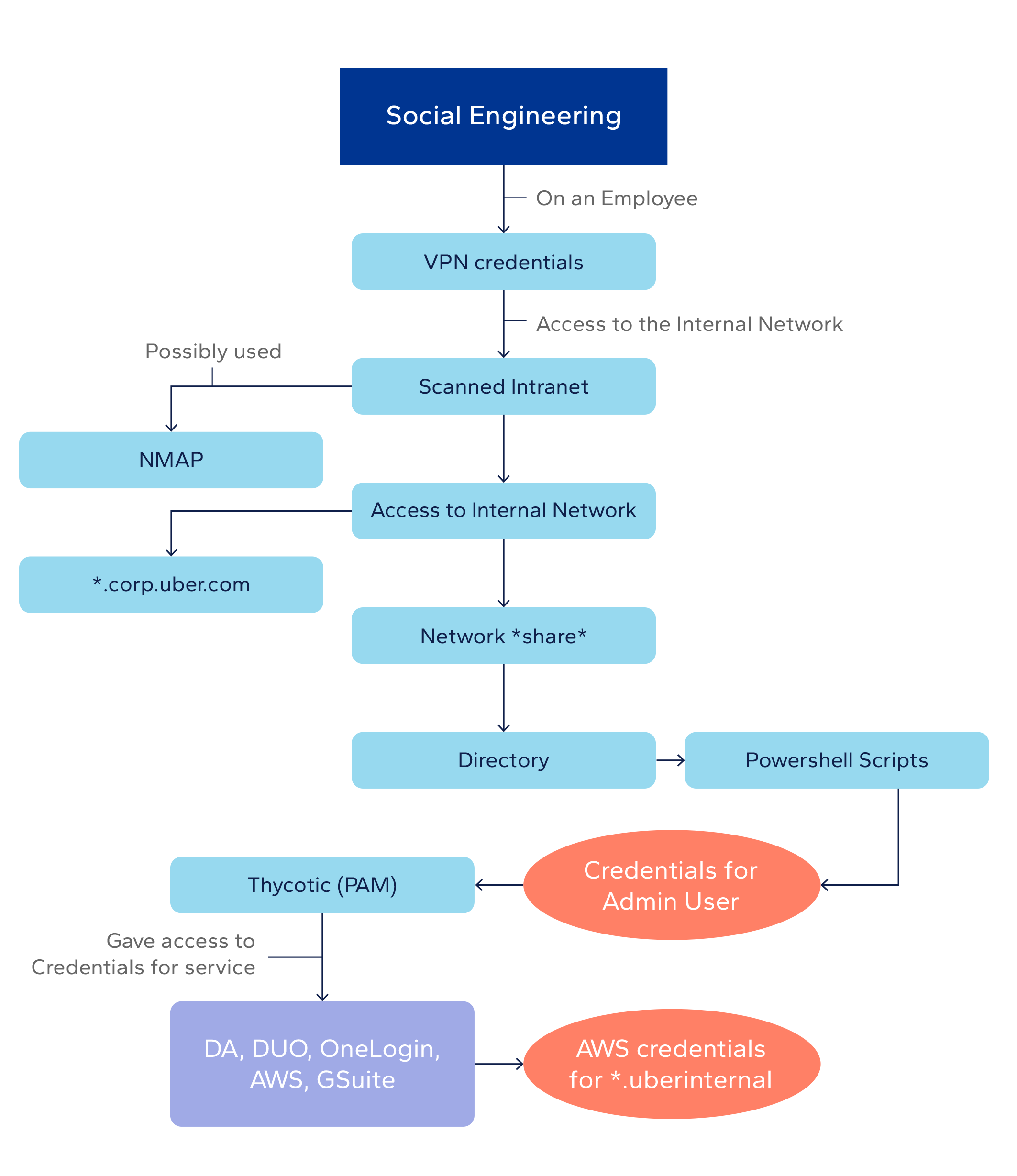
Source: DNV Cyber 2025

Responding to the attack
Uber took several measures to mitigate the 2022 incident and strengthen its security posture:
| Learning point | Comments |
|---|---|
Learning pointDo not use hardcode credentials in scripts |
CommentsThis is a major risk. Privileged credentials must be properly managed/vaulted and used dynamically whitin scripts. |
Learning pointEnforce least privilege |
CommentsToo much access makes things worse. The credentials the attackers found unlocked way too much. Limit access to only what is necessary. Following the principle of ‘least privilege’ could have limited the damage. |
Learning pointEnsure employee cybersecurity awareness as a critical pillar of sustained business resilience |
Comments
|
Learning pointUse credential management tools |
CommentsFor example, privileged access management (PAM) for password rotation and vaulting, while dynamically using within scripts. |
Learning pointMonitor for lateral movement |
Comments
|
Learning pointSecure internal tools and shares |
CommentsDo not leave sensitive scripts lying around. Always follow least privilege principles, encrypt secrets, and use secret managers or environment variables instead of embedding sensitive information in code. |
Broader lessons
“From an Identity and Access Management (IAM) perspective, the Uber breach exposed weak MFA protections, poor credential management, and excessive permissions. It reinforces the need for stronger authentication, the least privilege access, and secure handling of credentials to prevent similar attacks,” says Pascal van Vugt, Delivery Lead IAM, DNV Cyber. “Beyond the case-specific takeaways, the breach highlighted general challenges that an organization’s cybersecurity experts face around visibility, compliance and efficiency when designing and implementing robust IAM.”
| Challenge | Key questions |
|---|---|
ChallengeVisibility |
Key questions
|
ChallengeCompliance |
Key questions
|
ChallengeEfficiency |
Key questions
|
References
1 ‘Over two fifths of critical infrastructure organisations have suffered a cyber breach, report finds’, The Engineer, 5 August 2024 [online] www.theengineer.co.uk
2 ENERGY CYBER PRIORITY 2025: Addressing evolving risks, enabling transformation. DNV Cyber, 2025.
3 Security update. Uber Technologies, 19 September 2022 [online] www.uber.com

Whitepaper addressing the challenges of securing digital identities – both human and non-human

Free assessment that provides actionable insights and practical recommendations on your IAM posture

Real world examples how DNV Cyber has helped organizations overcome their IAM challenges

Expert reflections and comments on cybersecurity incidents

Who or what has access to what? The importance of securing digital identities