Frontline Insights: Lessons from a ransomware attack that also deleted backups
A ransomware attack on Company X not only encrypted important data but also deleted backups, leaving the company in a tough spot.
A ransomware attack on Company X not only encrypted important data but also deleted backups, leaving the company in a tough spot.
Cyberattacks are becoming more sophisticated, making strong cybersecurity measures essential. One alarming example is the ransomware attack on Company X, which not only encrypted important data but also deleted backups, leaving the company in a tough spot. This incident shows the need for strong Identity and Access Management (IAM) systems, especially for critical industries. This case highlights the importance of layered security measures and Privileged Access Management (PAM) capabilities.
Organizations across all sectors are bolstering their resilience to cyberattacks, which are becoming more common, complex and sophisticated. For example, the 2025 edition of DNV’s Energy Cyber Priority reports three-quarters of energy professionals saying their organizations have enhanced focus on cybersecurity because of growing geopolitical tensions over the last year.1

Nearly as many (72%) are concerned about the potential for attacks directed by foreign powers, up from 62% in 2023. But there is as much worry (71%) about the possibility of unintentional threat actors – for example, employees or supply-chain personnel – carelessly revealing details such as access passwords or responding to phishing emails. A slightly lower but majority share (62%) fears such security breaches may be deliberate acts by malicious insiders or former insiders, compared with 51% a year ago.
Such concerns indicate a need to widen the application of robust Identity and Access Management (IAM) that complies with regulations and meets business needs including empowering workers and suppliers to observe best practice in cybersecurity. Transformative digitization of many industries including energy is leading to exponential growth in the use of digital identities, and IAM focuses on handling these.
Cybersecurity training is now common in industries (e.g. energy) operating critical infrastructure (Figure 1), but there are still significant gaps in coverage, quality and continuity to close, and many organizations still struggle with even fairly immature IAM.
More training and preparation are needed to manage sophisticated cyberattacks
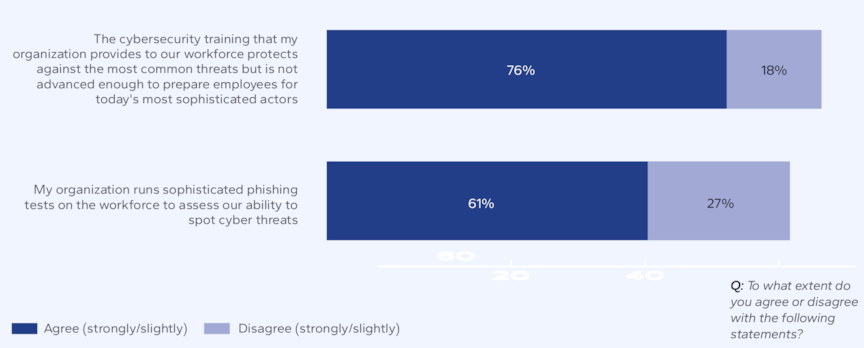
Source: DNV Cyber - Energy Cyber Priority 2025
Learning from the cybersecurity frontline
Optimizing IAM necessarily involves having a clear picture of existing and potential threats, and of how real-life attacks have developed and been handled. The expanding casebook includes many incidents, such as one in which an unnamed organization (‘company X’) was hit by a ransomware attack.
Despite the company’s wish to remain anonymous, the story of the attack is useful reading for those planning to govern access and to prepare for, prevent, detect and respond to attacks exploiting vulnerabilities in IAM. These stakeholders include those holding roles such as CIO, CISO, Head of IAM, Director IT and Cybersecurity, and so on. Many want to ensure regulatory compliance, but through IAM strategies that optimally balance identity security with overall cybersecurity strategy and aligns with specific business goals.

The attack and its impact
Company X’s internet-facing Windows Server was hacked. Once they gained access, the attackers scanned the network, then moved through it laterally. Administrator accounts were hacked by means as yet unknown or not divulged. Once they gained access, the attackers scanned the network then moved through it laterally. They made use of Microsoft’s PsExec tool to run executables on remote machines, causing damage. Ransomware binaries were executed, and target systems were encrypted. The attackers stole data and later published it.
Key takeaways
Key takeaways include making sure that the whole environment is designed with security in mind, using a layered and/or segmented approach to security boundaries. It is important to understand how IAM works as one component of the entire cybersecurity approach and, particularly in this case, how Privileged Access Management is used to protect privileged credentials and how, if or when they are compromised, it can mitigate further damage.
The PAM capabilities that would have been relevant in this case include:
“The learnings can be applied along with those from other case studies to optimize strategies to govern cybersecurity and to prepare for, prevent, detect, and respond to cyberattacks,” says Kari Vierimaa, Senior Security Consultant, DNV Cyber.
References
1 DNV Cyber (2025). ENERGY CYBER PRIORITY 2025: Addressing evolving risks, enabling transformation

Whitepaper addressing the challenges of securing digital identities – both human and non-human

Free assessment that provides actionable insights and practical recommendations on your IAM posture

Real world examples how DNV Cyber has helped organizations overcome their IAM challenges

Expert reflections and comments on cybersecurity incidents

Who or what has access to what? The importance of securing digital identities