Taking a three-step approach to operational technology cyber security risk reduction and incident responses
- Making operational technology (OT) cyber secure is ultimately about health and safety, the environment, and avoiding asset damage
- Making the cyber risks visible is key in a three-step approach to securing OT cyber security
- The approach involves knowing what OT you have, collaborating with physical domain experts, and responding with the industrial context in mind
- Coordinating with the industrial operations side must be part of the incident response playbook, urges DNV’s Håkon Olsen
Securing OT from cyber-attack is different from securing enterprise IT systems. Not because the technologies themselves are so different – but the consequences are. OT systems control many systems we rely on today, from oil tankers to high-speed trains, electricity grids, and nuclear power plants. Obviously, the consequences of hackers seizing control of the information and communication technology used to operate and safeguard such systems could be significantly worse than a data leak.
For most enterprise IT systems, the consequences of hacking are financial and sometimes also legal. The media regularly reports the fines levied at companies and government agencies for lack of privacy protection. Typically, such organizations have not done enough to block ‘unauthorized access to data’ or to stop ‘data being changed by an unauthorized individual’.
The most worrying consequences in the industrial sphere are physical; for example, a targeted attack could cause a major incident at an industrial plant, leaking poisonous chemicals into the surroundings or starting a huge fire. Damage to manufacturing equipment could disrupt important supply chains, causing shortages of critical goods such as fuels or food.
“Ultimately, OT cyber security is about saving lives, protecting the environment, and avoiding asset damage. In prioritizing the prevention of physical consequences from cyber-attacks on industrial assets, it is essential to use the tools that exist to make the cyber risks more visible,” Håkon Olsen, Principal Consultant - Cyber Security - OT Security - Incident Response, DNV.
These tools can be applied within a three-step approach to securing OT/IT, he adds: first, know what you have; second, make friends with physical domain experts; and third, respond with the industrial context in mind.
Step 1: Know what you have
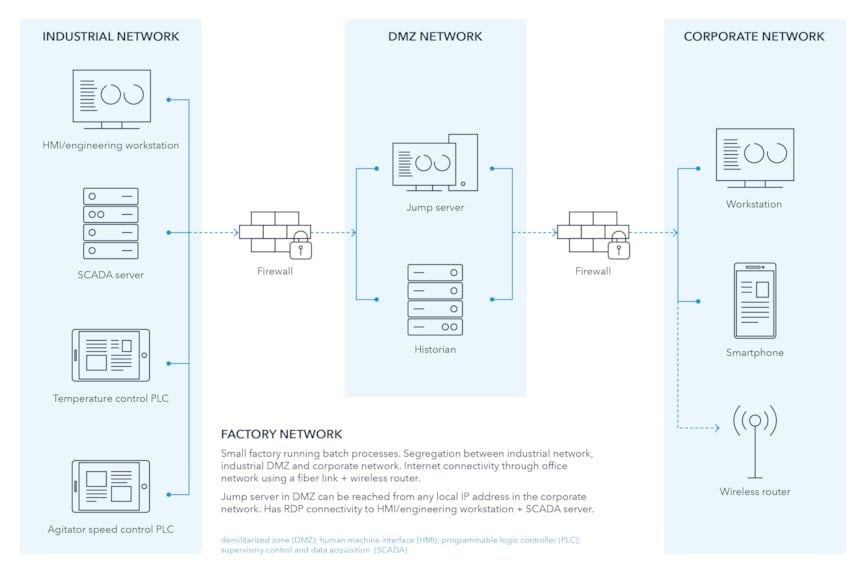
Your company needs to know what it has to be able to defend it. Hence, having visibility of the ‘network topology’ and ‘asset inventory’ are two essential tools for protecting OT/IT systems from cyber risk. A network topology is typically a drawing showing what the network consists of (Figure 1). Elements of this include, for example, network segments, servers, laptops, switches, and operational technology. OT includes any software interacting with an industrial plant’s sensors and controllers , such as programmable logic circuits (PLCs), pressure transmitters, and human-machine interfaces (HMIs).
An ‘asset inventory’ describes all hardware systems and the software that runs on them. In environments where things change frequently, this inventory should be generated dynamically. Often in OT systems, the inventory is a static file, such as an Excel spreadsheet, manually compiled by engineers during system design. This file is highly likely to become out-of-date over time due to a lack of updates when changes happen.
What is the ‘equipment under control’ doing?
Performing risk assessment based on network topology and asset inventory is commonplace. “But it is hard to connect this information to preventing specific physical consequences. We need to know what the ‘equipment under control’ is, and what it is used for,” says Olsen.
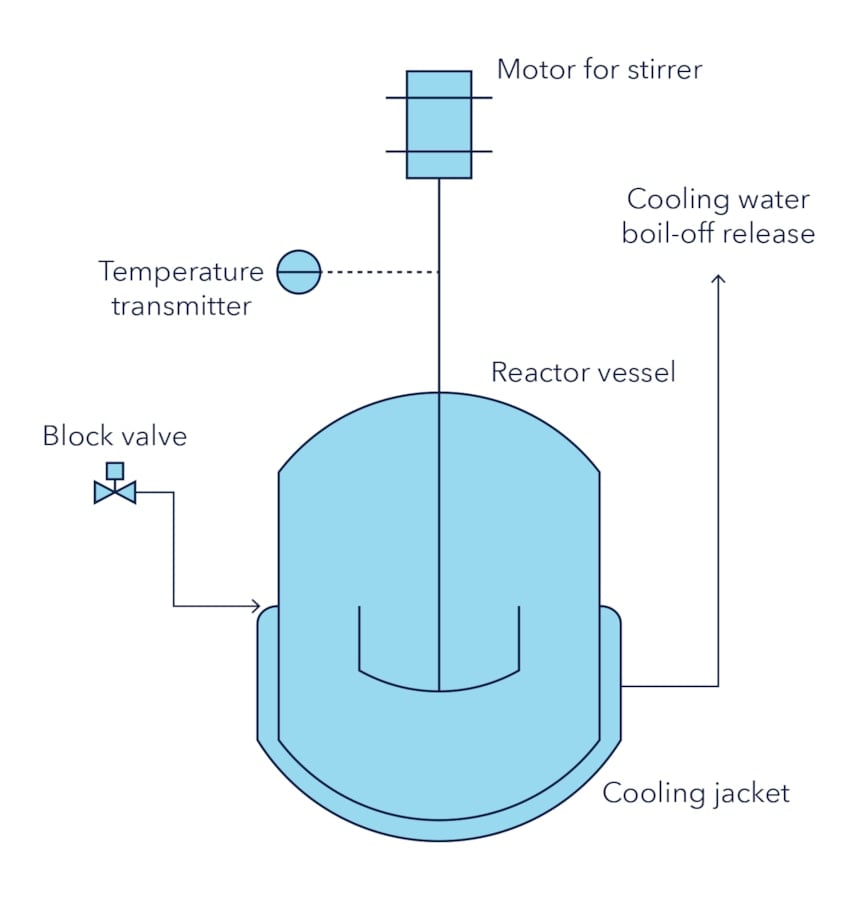
For example, the above network may operate a batch chemical reactor running an exothermic (heat-generating) reaction that requires cooling to avoid overheating and, if the products are gaseous, potential explosions. The information cannot be seen from the IT-type documentation alone; the experts need to connect this information to the physical world.
Imagine that the system in Figure 1 controls a reactor containing an exothermic reaction and that cooling water flows through a jacket around the reactor vessel. Based on temperature measurement, a controller opens and closes a valve to maintain a safe temperature. In Figure 1, this controller is the temperature-control PLC. Knowing this makes the physical risk visible.
Not knowing what the OT system controls can lead to focusing only on the ‘confidentiality, integrity and availability (CIA) triad’, without really considering the real consequences. These could be a severe explosion with potential health, safety, and environmental effects, and damage to neighbouring properties, Olsen explains.
“Unfortunately, lack of inventory control – especially when connecting industrial IT systems to the physical assets they control – is a very common problem across many industries,” he observes. “In summary, connecting the dots in your inventory means that for every server, switch, transmitter, PLC, and so on in your network, you need to know what jobs these items are a part of performing. Only then can you understand the potential consequences of a cyber-attack on the OT system.”
Step 2: Make friends with physical domain experts
Working in OT security means mastering great complexity. While someone may be an expert in industrial protocols, ladder logic programming, or building adversarial threat models, understanding the cyber security domain is itself a challenge.
“It is unrealistic to expect security experts to also be experts in all the physical domains they touch. You cannot expect OT security experts to know details of all technologies described as ‘equipment under control’ in ISO standards,” said Olsen. “Should a company’s Security Operation Center (SOC) analyst be both a trained chemical engineer and OT security expert, for instance? Obviously not. So, cyber risk assessments in industrial domains must be collaborative.”

Knowing the safety barriers is another important aspect of domain expertise. The example above lacks several safety features that would be mandatory in most locations. These features include having a passive pressure-relief system that works without the involvement of any digital technologies.
In many locations, it is also mandatory to have a process shutdown system comprising a control system with separate sensors, PLCs, and networks. This shutdown system intervenes to prevent the potential accident by using actuators installed purely for safety. This arrangement aims to avoid common cause failures between normal production systems and safety-critical systems. Being unaware of such systems can sometimes lead to OT security experts exaggerating, in good faith, the probability of the most severe consequences.
“So, it pays to make friends with domain experts. By involving the right domain expertise, you can get a realistic picture of the physical consequences of a scenario,” says Olsen.
Step 3: Plan responses with the industrial context in mind
As with an enterprise IT system, defending an industrial system against cyber-attack requires an incident response plan, but one that also takes the operational context into account. A key difference, though, is that for physical plants, the response plan may involve taking physical action, such as manually opening and closing valves. Obviously, this needs to be planned and exercised. If welding will be needed to handle the incident – for installing a new valve bypass, for example – coordinating with the industrial operations side has to be part of the incident response playbook.
Even attacks that do not affect OT systems directly may lead to operational changes in the industrial environment.1 “This bears lessons for us all. We need to think about how to minimize impact not just after an attack, but also during the response phase, which may be quite extensive,” says Olsen. “Scenario-based playbooks can be of immense help in planning and executing responses. The playbook should describe the scenario in sufficient detail to estimate affected systems and ask what it will take to return to operations if those systems will need taking out of service.”
The latter question would be difficult for an OT security expert to answer, he adds: “Again, you need domain expertise. In terms of the cyber incident response plan, you need information on who to contact during the response, who has the authority to decide when to move to the next steps, and so on. For example, if you need to switch to manual operations, say turning a valve, to continue with safe recovery of control system information and communications technology, this has to be part of your playbook.”
Even when viewing the challenges from an OT perspective, it is important to continue addressing the CIA triad: “We still need to ensure only authorized personnel have access to our systems. We need to ensure we protect data during transit and in storage, and we need to know that a packet storm is not going to take our industrial network down. The key message is that we need to articulate better the consequences of security breaches in the OT system,” concludes Olsen.
Summary: A three-step approach to securing OT/IT against cyber risk
Step 1: Know what you have. It is often not enough to know what IT components are in your system. You also need to know what they are controlling. This is important for understanding the risk related to a compromise of the asset, but also for planning how to respond to an attack.
Step 2: Make friends with domain experts. They can help you understand if a compromised asset could lead to a catastrophic scenario, and what it would take for an attacker to make that happen. Domain experts can also help you understand independent safety barriers that are part of the design, so that you do not exaggerate the probability of the worst-case scenarios.
Step 3: Plan your response with the industrial context in mind. Befriend and use the insight of domain experts to make practical playbooks – that may include physical actions that need to be taken on the factory floor by welders or process operators.
References
1 ‘Aluminum producer switches to manual operations after ransomware infection’, C Cimpanu, zdnet.com, 19 March 2019 [online]
